Page 142 - CA Inter Bhaskar Vol 1
P. 142
RISK ASSESSMENT AND INTERNAL CONTROL CA RAVI TAORI
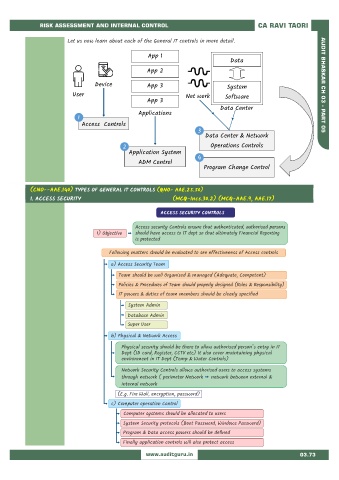
Let us now learn about each of the General IT controls in more detail.
App 1
Data
App 2
Device App 3 System AUDIT BHASKAR CH 03 - PART 05
User Net work Software
App 3
Data Center
Applications
1
Access Controls
3
Data Center & Network
2 Operations Controls
Application System
4
ADM Control
Program Change Control
(CNO--AAE.140) TYPES OF GENERAL IT CONTROLS (QNO- AAE.25.50)
1. ACCESS SECURITY (MCQ-Incs.30.2) (MCQ-AAE.9, AAE.17)
ACCESS SECURITY CONTROLS
Access security Controls ensure that authenticated, authorised persons
1) Objective should have access to IT dept so that ultimately Financial Reporting
is protected
Following matters should be evaluated to see effectiveness of Access controls
a) Access Security Team
Team should be well Organised & managed (Adequate, Competent)
Policies & Procedures of Team should properly designed (Roles & Responsibility)
IT powers & duties of team members should be clearly specified
System Admin
Database Admin
Super User
b) Physical & Network Access
Physical security should be there to allow authorised person's entry in IT
Dept (ID card, Register, CCTV etc) It also cover maintaining physical
environment in IT Dept (Temp & Water Controls)
Network Security Controls allows authorised users to access systems
through network ( perimeter Network network between external &
internal network
(E.g. Fire Wall, encryption, password)
c) Computer operation Control
Computer systems should be allocated to users
System Security protocols (Boot Password, Windows Password)
Program & Data access powers should be defined
Finally application controls will also protect access
www.auditguru.in 03.73